Continue cleaning up and update documentation
27
README.md
|
|
@ -1,4 +1,4 @@
|
|||
# T-Pot 17.10 (Beta)
|
||||
# T-Pot 17.10
|
||||
|
||||
This repository contains the necessary files to create the **[T-Pot](https://github.com/dtag-dev-sec/tpotce/releases)** ISO image.
|
||||
The image can then be used to install T-Pot on a physical or virtual machine.
|
||||
|
|
@ -6,9 +6,9 @@ The image can then be used to install T-Pot on a physical or virtual machine.
|
|||
In October 2016 we released
|
||||
[T-Pot 16.10](http://dtag-dev-sec.github.io/mediator/feature/2016/10/31/t-pot-16.10.html)
|
||||
|
||||
# T-Pot 17.10 (Beta)
|
||||
# T-Pot 17.10
|
||||
|
||||
T-Pot 17.10 uses latest 16.04 LTS Ubuntu Server Network Installer image, is based on
|
||||
T-Pot 17.10 runs on the latest 16.04 LTS Ubuntu Server Network Installer image, is based on
|
||||
|
||||
[docker](https://www.docker.com/), [docker-compose](https://docs.docker.com/compose/)
|
||||
|
||||
|
|
@ -112,18 +112,15 @@ Seeing is believing :bowtie:
|
|||
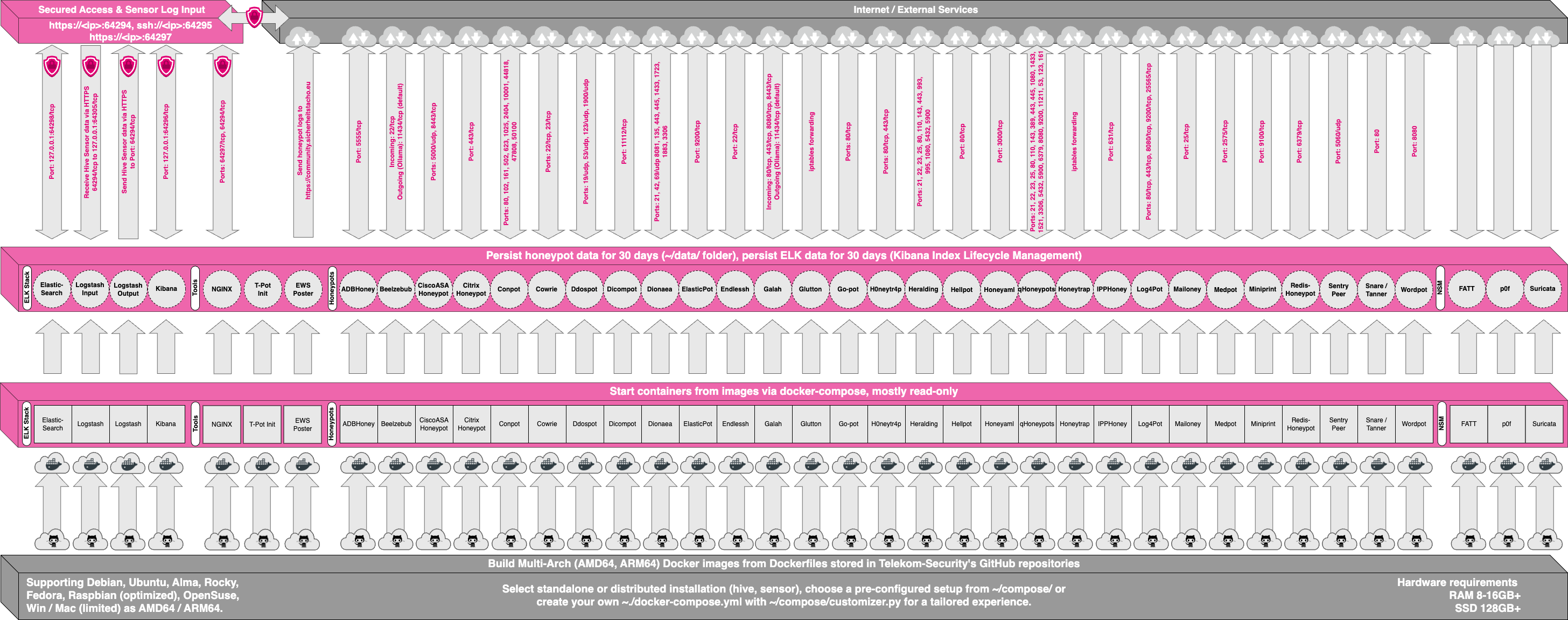
- **Persistence** is now enabled by default and will keep honeypot logs and tools data in `/data/` and its sub-folders by default for 30 days. You may change that behavior in `/opt/tpot/etc/logrotate/logrotate.conf`. ELK data however will be kept for 90 days by default. You may change that behavior in `/opt/tpot/etc/curator/actions.yml`. Scripts will be triggered through `/etc/crontab`.
|
||||
- **Updates**
|
||||
- **Docker** was updated to the latest **1.12.6** release within Ubuntu 16.04.x LTS
|
||||
- **ELK** was updated to the latest **Kibana 5.6.1**, **Elasticsearch 5.6.1** and **Logstash 5.6.1** releases.
|
||||
- **ELK** was updated to the latest **Kibana 5.6.3**, **Elasticsearch 5.6.3** and **Logstash 5.6.3** releases.
|
||||
- **Suricata** was updated to the latest **4.0.0** version including the latest **Emerging Threats** community ruleset.
|
||||
|
||||
- **Dashboards Makeover**
|
||||
- We now have **160+ Visualizations** pre-configured and compiled to 14 individual **Kibana Dashboards** for every honeypot. Monitor all *honeypot events* locally on your T-Pot installation. Aside from *honeypot events* you can also view *Suricata NSM, Syslog and NGINX* events for a quick overview of local host events.
|
||||
- View available IP reputation of any source IP address
|
||||
- View available CVE ID for events
|
||||
- More **Smart links** are now included.
|
||||
|
||||
- **Update Feature**
|
||||
- For the ones who like to live on the bleeding edge of T-Pot development there is now a update script available in `/opt/tpot/update.sh`. Just run the script and it will get the latest changes from the `master branch`. For now this feature is experimental and the first step to a true rolling release cycle.
|
||||
|
||||
- **Files & Folders**
|
||||
- While the `/data` folder is still in its old place, all T-Pot relevant files and folders have been restructured and will now be installed into `/opt/tpot`. Only a few system relevant files with regard to the installed OS and its services will be copied to locations outside the T-Pot base path.
|
||||
|
||||
|
|
@ -153,7 +150,7 @@ In T-Pot we combine the dockerized honeypots
|
|||
[Suricata](http://suricata-ids.org/) a Network Security Monitoring engine and
|
||||
[Wetty](https://github.com/krishnasrinivas/wetty) a web based SSH client.
|
||||
|
||||

|
||||
|
||||
|
||||
While data within docker containers is volatile we do now ensure a default 30 day persistence of all relevant honeypot and tool data in the well known `/data` folder and sub-folders. The persistence configuration may be adjusted in `/opt/tpot/etc/logrotate/logrotate.conf`. Once a docker container crashes, all other data produced within its environment is erased and a fresh instance is started from the corresponding docker image.<br>
|
||||
|
||||
|
|
@ -333,7 +330,7 @@ If you do not have a SSH client at hand and still want to access the machine via
|
|||
|
||||
and choose **WebTTY** from the navigation bar. You will be prompted to allow access for this connection and enter the password for the user **tsec**.
|
||||
|
||||

|
||||

|
||||
|
||||
<a name="kibana"></a>
|
||||
## Kibana Dashboard
|
||||
|
|
@ -344,16 +341,16 @@ Just open a web browser and access and connect to `https://<your.ip>:64297`, ent
|
|||
|
||||
and **Kibana** will automagically load. The Kibana dashboard can be customized to fit your needs. By default, we haven't added any filtering, because the filters depend on your setup. E.g. you might want to filter out your incoming administrative ssh connections and connections to update servers.
|
||||
|
||||

|
||||

|
||||
|
||||
<a name="tools"></a>
|
||||
## Tools
|
||||
We included some web based management tools to improve and ease up on your daily tasks.
|
||||
|
||||

|
||||

|
||||

|
||||

|
||||

|
||||

|
||||

|
||||
|
||||
|
||||
|
||||
<a name="maintenance"></a>
|
||||
|
|
@ -479,4 +476,4 @@ We will be releasing a new version of T-Pot about every 6-12 months.
|
|||
<a name="funfact"></a>
|
||||
# Fun Fact
|
||||
|
||||
Coffee just does not cut it anymore which is why we needed a different caffeine source and consumed *227* bottles of [Club Mate](https://de.wikipedia.org/wiki/Club-Mate) during the development of T-Pot 17.10 😇
|
||||
Coffee just does not cut it anymore which is why we needed a different caffeine source and consumed *242* bottles of [Club Mate](https://de.wikipedia.org/wiki/Club-Mate) during the development of T-Pot 17.10 😇
|
||||
|
|
|
|||
|
Before Width: | Height: | Size: 387 KiB After Width: | Height: | Size: 284 KiB |
|
|
@ -1,4 +1,11 @@
|
|||
[](https://microbadger.com/images/dtagdevsec/p0f:1706 "Get your own version badge on microbadger.com") [](https://microbadger.com/images/dtagdevsec/p0f:1706 "Get your own image badge on microbadger.com")
|
||||
[](https://microbadger.com/images/dtagdevsec/p0f:1710 "Get your own version badge on microbadger.com") [](https://microbadger.com/images/dtagdevsec/p0f:1710 "Get your own image badge on microbadger.com")
|
||||
|
||||
# dockerized p0f
|
||||
|
||||
[p0f](http://lcamtuf.coredump.cx/p0f3/) P0f is a tool that utilizes an array of sophisticated, purely passive traffic fingerprinting mechanisms to identify the players behind any incidental TCP/IP communications (often as little as a single normal SYN) without interfering in any way.
|
||||
|
||||
This dockerized version is part of the **[T-Pot community honeypot](http://dtag-dev-sec.github.io/)** of Deutsche Telekom AG.
|
||||
|
||||
The `Dockerfile` contains the blueprint for the dockerized p0f and will be used to setup the docker image.
|
||||
|
||||
The `docker-compose.yml` contains the necessary settings to test p0f using `docker-compose`. This will ensure to start the docker container with the appropriate permissions and port mappings.
|
||||
|
|
|
|||
12
docker/p0f/docker-compose.yml
Normal file
|
|
@ -0,0 +1,12 @@
|
|||
version: '2.1'
|
||||
|
||||
services:
|
||||
|
||||
# P0f service
|
||||
p0f:
|
||||
container_name: p0f
|
||||
restart: always
|
||||
network_mode: "host"
|
||||
image: "dtagdevsec/p0f:1710"
|
||||
volumes:
|
||||
- /data/p0f/log:/var/log/p0f
|
||||
|
|
@ -1,31 +1,15 @@
|
|||
[](https://microbadger.com/images/dtagdevsec/suricata:1706 "Get your own version badge on microbadger.com") [](https://microbadger.com/images/dtagdevsec/suricata:1706 "Get your own image badge on microbadger.com")
|
||||
[](https://microbadger.com/images/dtagdevsec/suricata:1710 "Get your own version badge on microbadger.com") [](https://microbadger.com/images/dtagdevsec/suricata:1710 "Get your own image badge on microbadger.com")
|
||||
|
||||
# dockerized suricata
|
||||
|
||||
|
||||
[suricata](http://suricata-ids.org/) is a Network IDS, IPS and Network Security Monitoring engine.
|
||||
|
||||
This repository contains the necessary files to create a *dockerized* version of suricata.
|
||||
|
||||
This dockerized version is part of the **[T-Pot community honeypot](http://dtag-dev-sec.github.io/)** of Deutsche Telekom AG.
|
||||
|
||||
The `Dockerfile` contains the blueprint for the dockerized suricata and will be used to setup the docker image.
|
||||
|
||||
The `suricata.yaml` is tailored to fit the T-Pot environment.
|
||||
|
||||
The `supervisord.conf` is used to start suricata under supervision of supervisord.
|
||||
|
||||
Using systemd, copy the `systemd/suricata.service` to `/etc/systemd/system/suricata.service` and start using
|
||||
|
||||
```
|
||||
systemctl enable suricata
|
||||
systemctl start suricata
|
||||
```
|
||||
|
||||
This will make sure that the docker container is started with the appropriate permissions and port mappings. Further, it autostarts during boot.
|
||||
|
||||
By default all data will be stored in `/data/suricata/` until the service will be restarted which is by default every 24 hours. If you want to keep data persistently simply edit the ``service`` file, find the line that contains ``clean.sh`` and set the option from ``off`` to ``on``. Be advised to establish some sort of log management if you wish to do so.
|
||||
The `docker-compose.yml` contains the necessary settings to test suricata using `docker-compose`. This will ensure to start the docker container with the appropriate permissions.
|
||||
|
||||
# Suricata Dashboard
|
||||
|
||||

|
||||

|
||||
|
|
|
|||
|
Before Width: | Height: | Size: 781 KiB After Width: | Height: | Size: 542 KiB |
18
docker/suricata/docker-compose.yml
Normal file
|
|
@ -0,0 +1,18 @@
|
|||
# T-Pot (Standard)
|
||||
# For docker-compose ...
|
||||
version: '2.1'
|
||||
|
||||
services:
|
||||
|
||||
# Suricata service
|
||||
suricata:
|
||||
container_name: suricata
|
||||
restart: always
|
||||
network_mode: "host"
|
||||
cap_add:
|
||||
- NET_ADMIN
|
||||
- SYS_NICE
|
||||
- NET_RAW
|
||||
image: "dtagdevsec/suricata:1710"
|
||||
volumes:
|
||||
- /data/suricata/log:/var/log/suricata
|
||||
|
|
@ -1,6 +1,5 @@
|
|||
FROM portainer/portainer:latest
|
||||
|
||||
ADD favicon.ico /ico
|
||||
#ADD small.png /images/logo.png
|
||||
|
||||
ENTRYPOINT ["/portainer"]
|
||||
|
|
|
|||
|
|
@ -1,26 +1,15 @@
|
|||
# dockerized portainer (ui-for-docker)
|
||||
[](https://microbadger.com/images/dtagdevsec/ui-for-docker:1710 "Get your own version badge on microbadger.com") [](https://microbadger.com/images/dtagdevsec/ui-for-docker:1710 "Get your own image badge on microbadger.com")
|
||||
|
||||
# portainer
|
||||
|
||||
[portainer](http://portainer.io/) Portainer allows you to manage your Docker containers, images, volumes, networks and more ! It is compatible with the standalone Docker engine and with Docker Swarm.
|
||||
|
||||
This repository contains the necessary files to create a *dockerized* version of portainer.
|
||||
|
||||
This dockerized version is part of the **[T-Pot community honeypot](http://dtag-dev-sec.github.io/)** of Deutsche Telekom AG.
|
||||
|
||||
The `Dockerfile` contains the blueprint for the dockerized portainer and will be used to setup the docker image.
|
||||
|
||||
Using systemd, copy the `systemd/ui-for-docker.service` to `/etc/systemd/system/ui-for-docker.service` and start using
|
||||
The `docker-compose.yml` contains the necessary settings to test portainer using `docker-compose`. This will ensure to start the docker container with the appropriate permissions and port mappings.
|
||||
|
||||
```
|
||||
systemctl enable ui-for-docker
|
||||
systemctl start ui-for-docker
|
||||
```
|
||||
# Portainer UI
|
||||
|
||||
This will make sure that the docker container is started with the appropriate permissions and port mappings. Further, it autostarts during boot.
|
||||
|
||||
# Portainer Dashboard
|
||||
|
||||

|
||||

|
||||

|
||||

|
||||

|
||||

|
||||
|
|
|
|||
BIN
docker/ui-for-docker/doc/dashboard.png
Normal file
|
After Width: | Height: | Size: 224 KiB |
|
Before Width: | Height: | Size: 91 KiB |
|
Before Width: | Height: | Size: 155 KiB |
|
Before Width: | Height: | Size: 123 KiB |
|
Before Width: | Height: | Size: 302 KiB |
|
Before Width: | Height: | Size: 103 KiB |
21
docker/ui-for-docker/docker-compose.yml
Normal file
|
|
@ -0,0 +1,21 @@
|
|||
# T-Pot (Standard)
|
||||
# For docker-compose ...
|
||||
version: '2.1'
|
||||
|
||||
networks:
|
||||
ui-for-docker_local:
|
||||
|
||||
services:
|
||||
|
||||
# Ui-for-docker service
|
||||
ui-for-docker:
|
||||
container_name: ui-for-docker
|
||||
command: -H unix:///var/run/docker.sock --no-auth
|
||||
restart: always
|
||||
networks:
|
||||
- ui-for-docker_local
|
||||
ports:
|
||||
- "127.0.0.1:64299:9000"
|
||||
image: "dtagdevsec/ui-for-docker:1710"
|
||||
volumes:
|
||||
- /var/run/docker.sock:/var/run/docker.sock
|
||||
|
Before Width: | Height: | Size: 5.9 KiB |
|
|
@ -1,14 +0,0 @@
|
|||
[Unit]
|
||||
Description=ui-for-docker
|
||||
Requires=docker.service
|
||||
After=docker.service
|
||||
|
||||
[Service]
|
||||
Restart=always
|
||||
ExecStartPre=-/usr/bin/docker stop ui-for-docker
|
||||
ExecStartPre=-/usr/bin/docker rm -v ui-for-docker
|
||||
ExecStart=/usr/bin/docker run --name ui-for-docker --rm=true -v /var/run/docker.sock:/var/run/docker.sock -p 127.0.0.1:64299:9000 dtagdevsec/ui-for-docker:1706 -H unix:///var/run/docker.sock --no-auth
|
||||
ExecStop=/usr/bin/docker stop ui-for-docker
|
||||
|
||||
[Install]
|
||||
WantedBy=multi-user.target
|
||||
|
|
@ -1,4 +1,15 @@
|
|||
[](https://microbadger.com/images/dtagdevsec/vnclowpot:1706 "Get your own version badge on microbadger.com") [](https://microbadger.com/images/dtagdevsec/vnclowpot:1706 "Get your own image badge on microbadger.com")
|
||||
[](https://microbadger.com/images/dtagdevsec/vnclowpot:1710 "Get your own version badge on microbadger.com") [](https://microbadger.com/images/dtagdevsec/vnclowpot:1710 "Get your own image badge on microbadger.com")
|
||||
|
||||
# vnclowpot
|
||||
|
||||
[vnclowpot](https://github.com/magisterquis/vnclowpot) is a low-interaction VNC honeypot with a static challenge.
|
||||
|
||||
This dockerized version is part of the **[T-Pot community honeypot](http://dtag-dev-sec.github.io/)** of Deutsche Telekom AG.
|
||||
|
||||
The `Dockerfile` contains the blueprint for the dockerized vnclowpot and will be used to setup the docker image.
|
||||
|
||||
The `docker-compose.yml` contains the necessary settings to test vnclowpot using `docker-compose`. This will ensure to start the docker container with the appropriate permissions and port mappings.
|
||||
|
||||
# vnclowpot Dashboard
|
||||
|
||||

|
||||
|
|
|
|||
BIN
docker/vnclowpot/doc/dashboard.png
Normal file
|
After Width: | Height: | Size: 333 KiB |
|
|
@ -13,6 +13,6 @@ services:
|
|||
- vnclowpot_local
|
||||
ports:
|
||||
- "5900:5900"
|
||||
image: "dtagdevsec/vnclowpot:1706"
|
||||
image: "dtagdevsec/vnclowpot:1710"
|
||||
volumes:
|
||||
- /data/vnclowpot/log:/var/log/vnclowpot
|
||||
|
|
|
|||